1.配置ForwardAuth(转发认证)的服务Service
首先,我们找到需要进行ForwardAuth(转发认证)的服务,我们下面以一个外部的OpenWrt服务进行举例:
apiVersion: v1
kind: Service
metadata:
name: openwrt-service
namespace: openwrt
spec:
type: ClusterIP
ports:
- name: http
port: 80
targetPort: 80
---
apiVersion: discovery.k8s.io/v1
kind: EndpointSlice
metadata:
name: openwrt-service
namespace: openwrt
labels:
kubernetes.io/service-name: openwrt-service
addressType: IPv4
ports:
- name: http
port: 80
protocol: TCP
endpoints:
- addresses:
- 192.168.1.1
conditions: # 注意必须要加这个才能被Traefik抓取到
ready: true
2.目标服务IngressRoute规则配置
在配置好这个服务之后,我们会给它配置一个IngressRoute规则,外部可以基于域名openwrt.example.com的方式进行访问OpenWrt服务:
apiVersion: traefik.io/v1alpha1
kind: IngressRoute
metadata:
name: openwrt-http
namespace: openwrt
spec:
entryPoints:
- web
routes:
- kind: Rule
match: Host(`openwrt.example.com`)
services:
- name: openwrt-service
port: 80
3.Authentik创建一个ForwardAuth应用
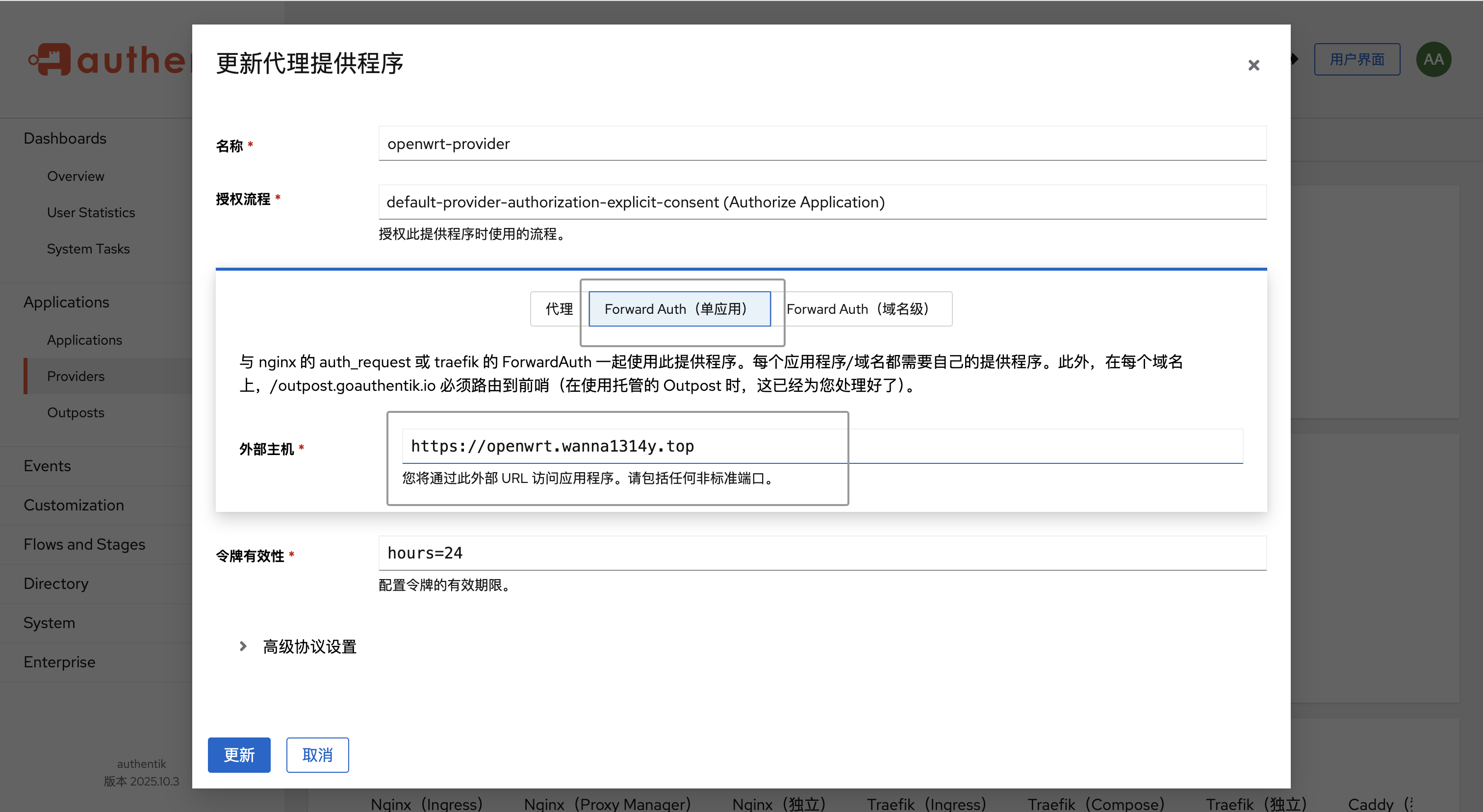
先是正常创建Authentik的Application和Provider,对于Provider创建的时候,类型选择Proxy Provider,并配置好要进行验证的域名URL地址。
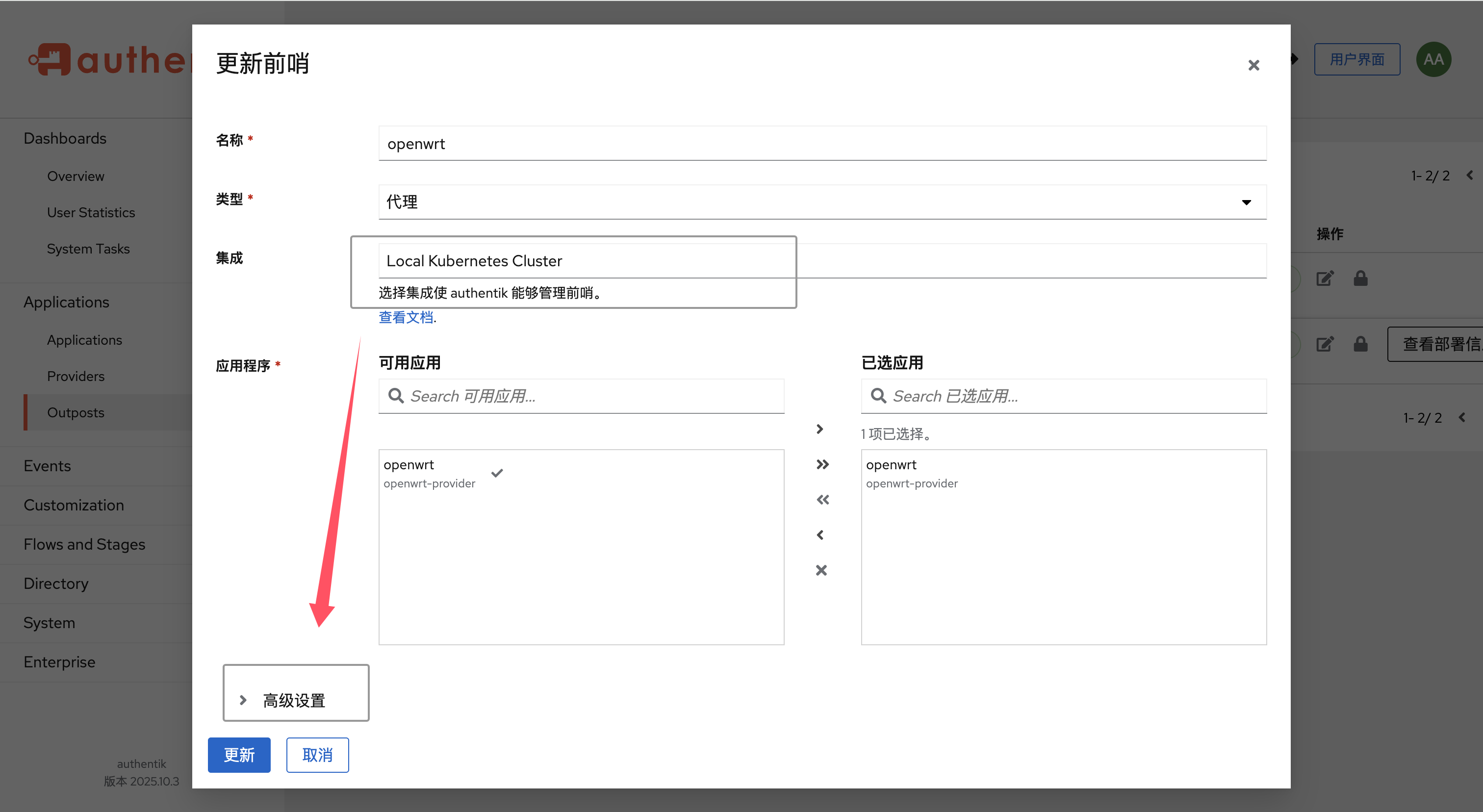
4.创建Authentik的Outpost前哨规则
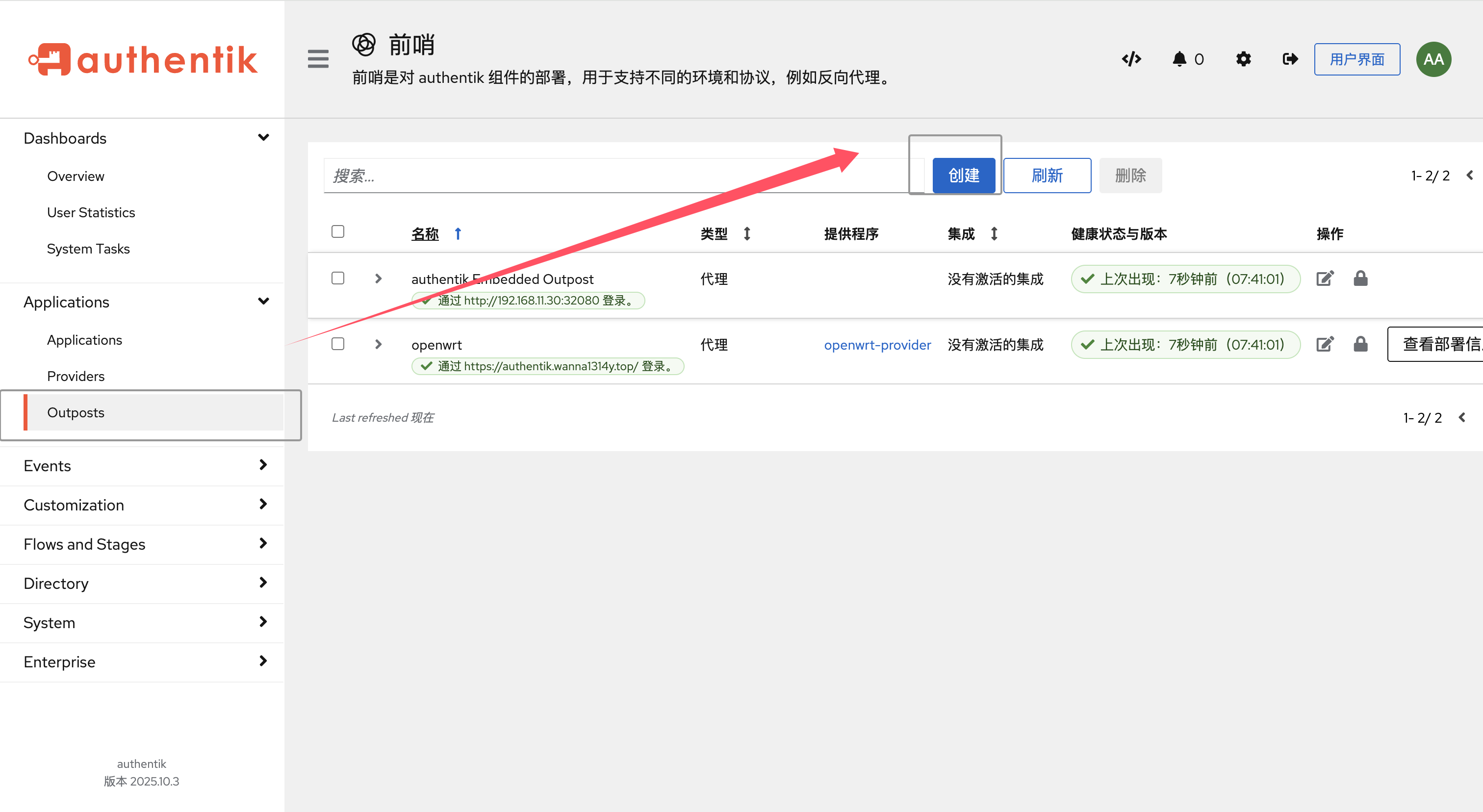
以此选择Outposts-创建,去进行Outpost的创建:
接着,集成这里,可以选择K8S直接集成,很简单,点确认就完成了,但是似乎所有的服务都必须在authentik这个Namespace下,好像不太优雅,没找到什么优雅的方案;也可以不选,然后后续手动创建Proxy服务。如果直接使用K8S集成的话,记得修改高级选项当中的配置;我们这里不选,然后手动创建Proxy服务。
参考官方文档:https://next.goauthentik.io/add-secure-apps/outposts/manual-deploy-kubernetes/
apiVersion: v1
kind: Secret
metadata:
labels:
app.kubernetes.io/instance: __OUTPOST_NAME__
app.kubernetes.io/name: authentik-outpost
name: authentik-outpost-api
namespace: __NAMESPACE__
type: Opaque
stringData:
AUTHENTIK_HOST: "__AUTHENTIK_URL__"
AUTHENTIK_INSECURE: "true"
AUTHENTIK_TOKEN: "__AUTHENTIK_TOKEN__"
---
apiVersion: v1
kind: Service
metadata:
labels:
app.kubernetes.io/instance: __OUTPOST_NAME__
app.kubernetes.io/name: authentik-outpost
name: authentik-outpost
namespace: __NAMESPACE__
spec:
ports:
- name: http
port: 9000
protocol: TCP
targetPort: http
- name: https
port: 9443
protocol: TCP
targetPort: https
type: ClusterIP
selector:
app.kubernetes.io/instance: __OUTPOST_NAME__
app.kubernetes.io/name: authentik-outpost
---
apiVersion: apps/v1
kind: Deployment
metadata:
labels:
app.kubernetes.io/instance: __OUTPOST_NAME__
app.kubernetes.io/name: authentik-outpost
name: authentik-outpost
namespace: __NAMESPACE__
spec:
selector:
matchLabels:
app.kubernetes.io/instance: __OUTPOST_NAME__
app.kubernetes.io/name: authentik-outpost
template:
metadata:
labels:
app.kubernetes.io/instance: __OUTPOST_NAME__
app.kubernetes.io/name: authentik-outpost
spec:
containers:
- image: ghcr.io/goauthentik/proxy:{__VERSION__}
name: proxy
ports:
- containerPort: 9000
name: http
protocol: TCP
- containerPort: 9443
name: https
protocol: TCP
envFrom:
- secretRef:
name: authentik-outpost-api
---
apiVersion: traefik.io/v1alpha1
kind: Middleware
metadata:
labels:
app.kubernetes.io/instance: __OUTPOST_NAME__
app.kubernetes.io/managed-by: goauthentik.io
app.kubernetes.io/name: authentik-proxy
app.kubernetes.io/version: __VERSION__
goauthentik.io/outpost-name: __OUTPOST_NAME__
goauthentik.io/outpost-type: proxy
goauthentik.io/outpost-uuid: c817db1b2fd947cc817c9a80baa1e83f
name: ak-outpost
namespace: __NAMESPACE__
spec:
forwardAuth:
address: http://authentik-outpost:9000/outpost.goauthentik.io/auth/traefik
authResponseHeaders:
- X-authentik-username
- X-authentik-groups
- X-authentik-entitlements
- X-authentik-email
- X-authentik-name
- X-authentik-uid
- X-authentik-jwt
- X-authentik-meta-jwks
- X-authentik-meta-outpost
- X-authentik-meta-provider
- X-authentik-meta-app
- X-authentik-meta-version
authResponseHeadersRegex: ""
trustForwardHeader: true
一共有如下几个变量需要替换:
- OUTPOST_NAME,前哨的名称,根据刚刚创建前哨时候的name进行填写。
- NAMESPACE,这些相关的服务要部署的Namespace,我这里直接部署在openwrt的Namespace下。
- VERSION,Authentik服务的版本,例如2025.10.3。
- AUTHENTIK_URL,你的Authentik服务的URL地址,例如
https://authentik.example.com。 - AUTHENTIK_TOKEN,Authentik服务创建前哨时的Token,注意在跳过K8S集成之后,前哨创建成功之后,查看部署信息可以找到Token,粘贴进来即可。
5.修改服务IngressRoute规则配置ForwardAuth中间件
新增middlewares的配置项,名称和我们刚刚创建的Middleware中间件名称能对应上即可。
middlewares:
- name: ak-outpost-openwrt
完整的配置参考:
apiVersion: traefik.io/v1alpha1
kind: IngressRoute
metadata:
name: openwrt-http
namespace: openwrt
spec:
entryPoints:
- web
routes:
- kind: Rule
match: Host(`openwrt.example.com`)
# 配置Authentik的Outpost中间件, 拦截请求进行登录认证
middlewares:
- name: ak-outpost-openwrt
services:
- name: openwrt-service
port: 80
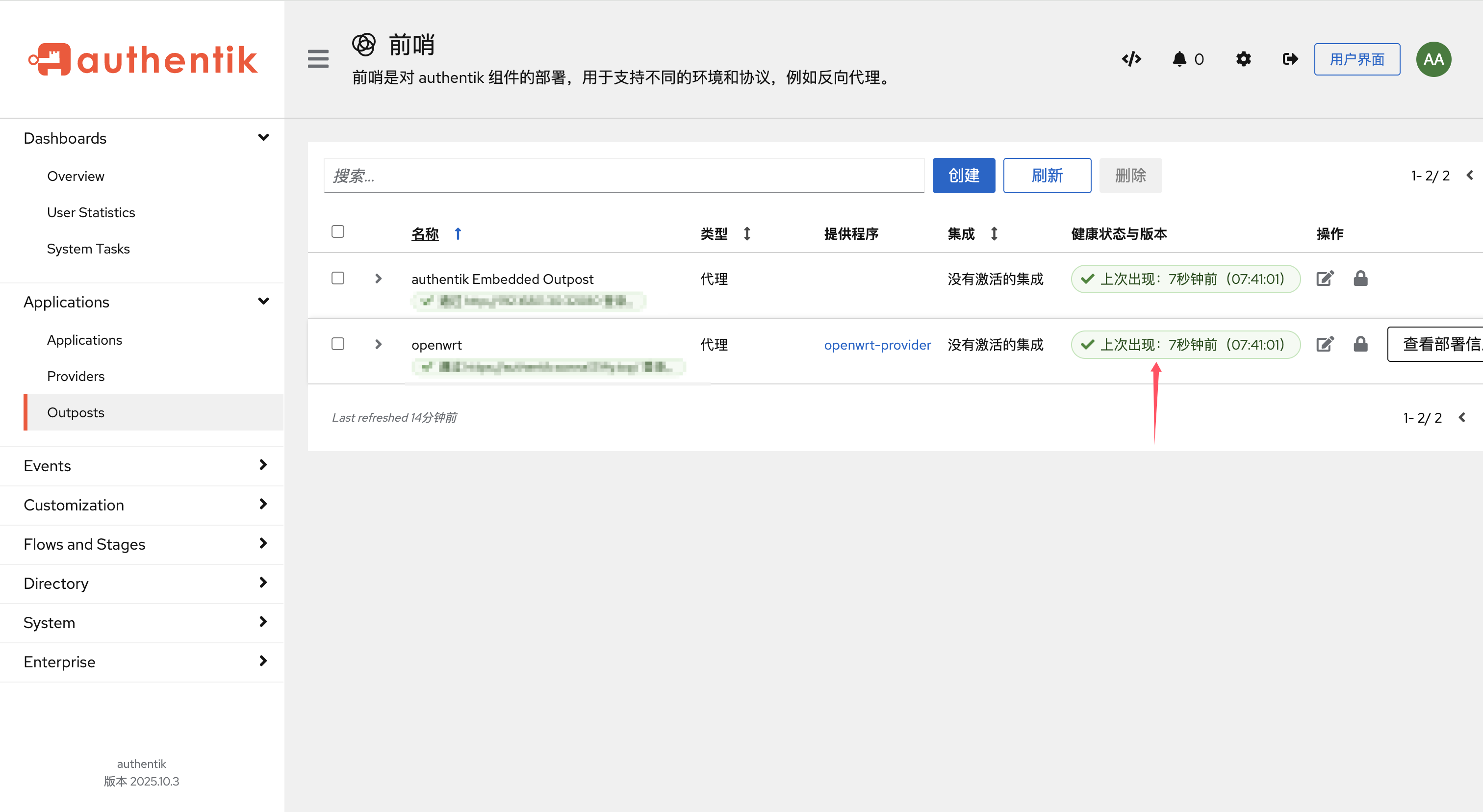
配置完成之后,如果没什么问题,在Authentik的Outposts当中可以看到我们配置没问题。
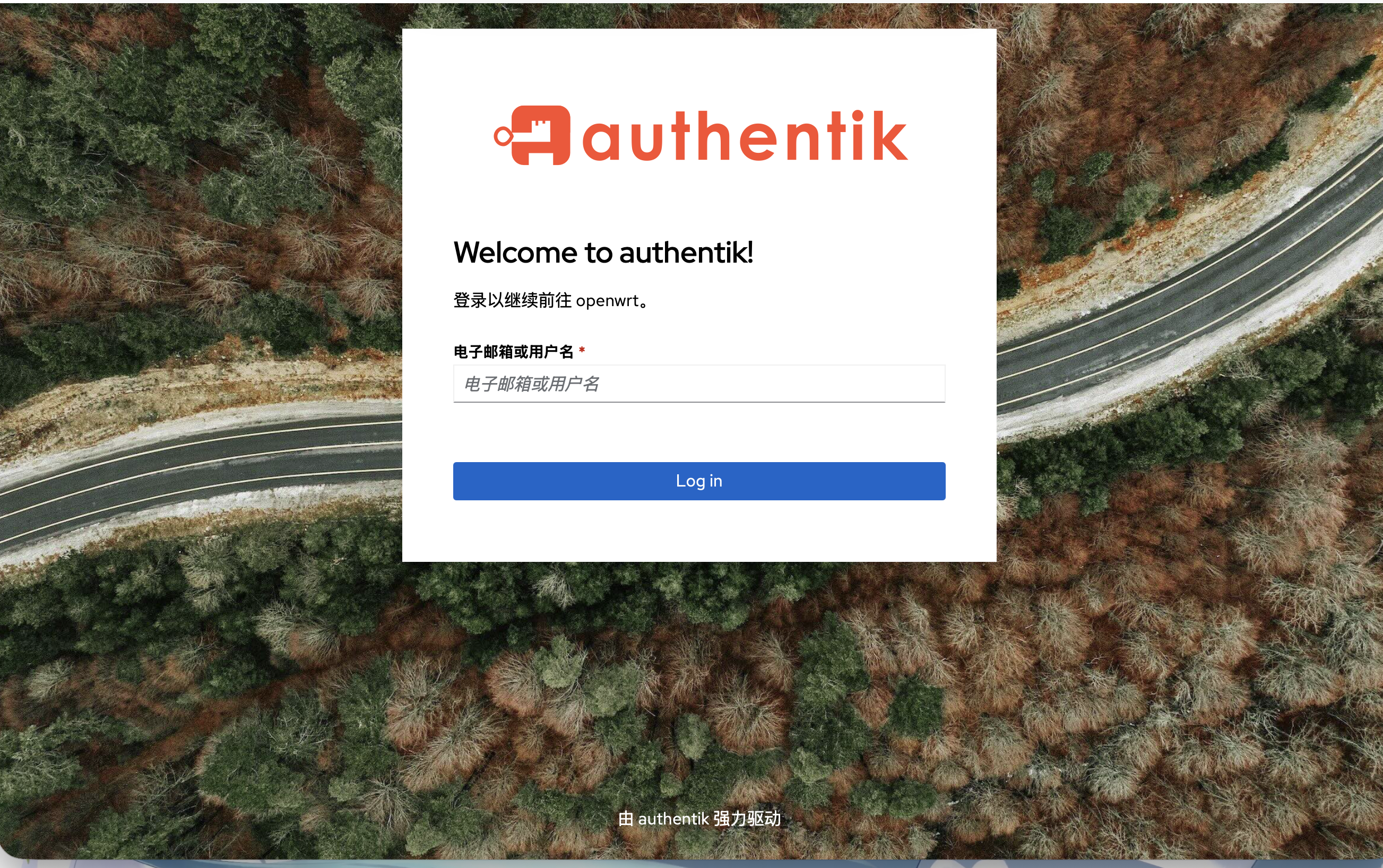
接着我们访问我们的目标服务的域名,确认请求页面确实被Authentik所拦截下来,都这里我们的ForwardAuth转发认证的配置就完成啦。
评论